PREVIOUS ARTICLENEXT ARTICLE
NEWS
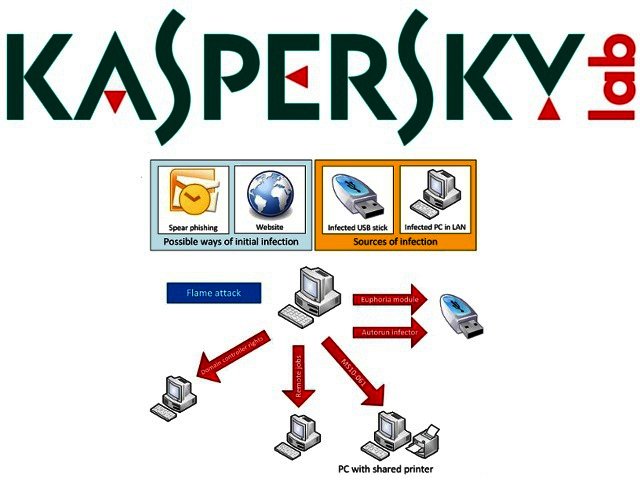
Kaspersky Lab believes Stuxnet and Flame developers connected
By Staff Writer 12 June 2012 | Categories: news
After sinkholing most of the malicious domains used by Flame, Kaspersky Lab has now revealed further information about “the most complex cyber-weapon to date”.
According to the Russian anti-virus firm, at the time of its discovery, there was no strong evidence of Flame being developed by the same team that delivered Stuxnet and Duqu. The approach to the development of Flame and Duqu/Stuxnet was different as well, which lead to the conclusion that these projects were created by separate teams.
However, the following research, conducted by Kaspersky Lab, reveals that these teams in fact cooperated at least once during the early stages of development.
New findings
The earliest known version of Stuxnet, supposedly created in June 2009, contains a special module known as “Resource 207”. In the subsequent 2010 version of Stuxnet this module was completely removed. The “Resource 207” module is an encrypted DLL file and it contains an executable file that’s the size of 351,768 bytes with the name “atmpsvcn.ocx”.
This particular file, as it is now revealed by Kaspersky Lab’s investigation, has a lot in common with the code used in Flame. The list of striking resemblances includes the names of mutually exclusive objects, the algorithm used to decrypt strings, and the similar approaches to file naming.
More than that, most sections of code appear to be identical or similar in the respective Stuxnet and Flame modules, which leads to the conclusion that the exchange between Flame and the Duqu/Stuxnet teams was done in a form of source code (i.e. not in binary form).
The primary functionality of the Stuxnet “Resource 207” module was distributing the infection from one machine to another, using the removable USB drives and exploiting the vulnerability in Windows kernel to obtain escalation of privileges within the system. The code which is responsible for distribution of malware using USB drives is completely identical to the one used in Flame.
Alexander Gostev, chief security expert at Kaspersky Lab, comments: “Despite the newly discovered facts, we are confident that Flame and Tilded are completely different platforms, used to develop multiple cyber-weapons. They each have different architectures with their own unique tricks that were used to infect systems and execute primary tasks. The projects were indeed separate and independent from each other. However, the new findings that reveal how the teams shared source code of at least one module in the early stages of development prove that the groups cooperated at least once.What we have found is very strong evidence that Stuxnet/Duqu and Flame cyber-weapons are connected.”
A recent report in the New York Times linked both Israel and the United States of America to the development of the Stuxnet worm. Targeting Iran’s nuclear facilities, the virus went public in 2010 due to an apparent programming error.
Background
According to Kaspersky, Stuxnet was the first cyber-weapon targeting industrial facilities. The fact that Stuxnet also infected regular PCs worldwide led to its discovery in June 2010, although the earliest known version of the malicious program was created one year before that. The next example of a cyber-weapon, now known as Duqu, was found in September 2011. Unlike Stuxnet, the main task of the Duqu Trojan was to serve as a backdoor to the infected system and steal private information (cyber-espionage).
During the analysis of Duqu, strong similarities were discovered with Stuxnet, which revealed that the two cyber-weapons were created using the same attack platform known as the “Tilded Platform”. The name originated from the preferences of the malware developers for filenames of the form “~d*.*” – hence, “Tilde-d”.
The Flame malware, discovered in May 2012 following the investigation prompted by International Communications Union (ITU) and conducted by Kaspersky Lab, was, at first sight, entirely different. Some features, such as the size of the malicious program, the use of LUA programming language and its diverse functionality, all indicated that Flame was not connected to Duqu or Stuxnet’s creators.
However, the new facts that have emerged completely re-write the history of Stuxnet and prove without a doubt, that the “Tilded” platform is indeed connected to the Flame platform.
Further details about the investigation can be found in the article at http://www.securelist.com/en/blog?weblogid=208193568. To learn more about Flame malware refer to the Flame FAQ prepared by Kaspersky Lab’s security researchers.
USER COMMENTS
Most Read Articles
Read

Magazine Online
TechSmart.co.za is South Africa's leading magazine for tech product reviews, tech news, videos, tech specs and gadgets.
Start reading now >
Download latest issue
Have Your Say
What new tech or developments are you most anticipating this year?
New smartphone announcements (46 votes)
Technological breakthroughs (29 votes)
Launch of new consoles, or notebooks (14 votes)
Innovative Artificial Intelligence solutions (29 votes)
Biotechnology or medical advancements (24 votes)
Better business applications (160 votes)



